Cloud Security
The first question that Raul asked us was "What is the cloud?". Raul defined the cloud as an infrastructure that has no security itself. Public clouds such as Amazon Web Services and Azure offer IaaS services that give us flexibility, immediacy, and ease, but they are not safe; we have to protect ourselves.
Next, he introduced the difference between a traditional firewall and a firewall designed for the cloud. He gave the example of the process of publishing a new application. In the case of a traditional firewall, it is necessary to specify a rule to allow this new application, which slows down the publication process for developers, it is a "stopper". In the cloud, all elements see each other so it is necessary to establish the desired traffic flows. The firewall does not work at the IP level, it uses objects and receives feed from all environments to automatically adapt to changes. This new way of working provides agility, allowing the publication process to be almost instantaneous.
A concept that he explained was "auto-scaling", the growth of the solution in a specific moment triggered by the momentaneous necessities. Cloud services allow us not to pay today for what we will use tomorrow; we pay for the use we make. This auto-scaling is done automatically thanks to APIs.
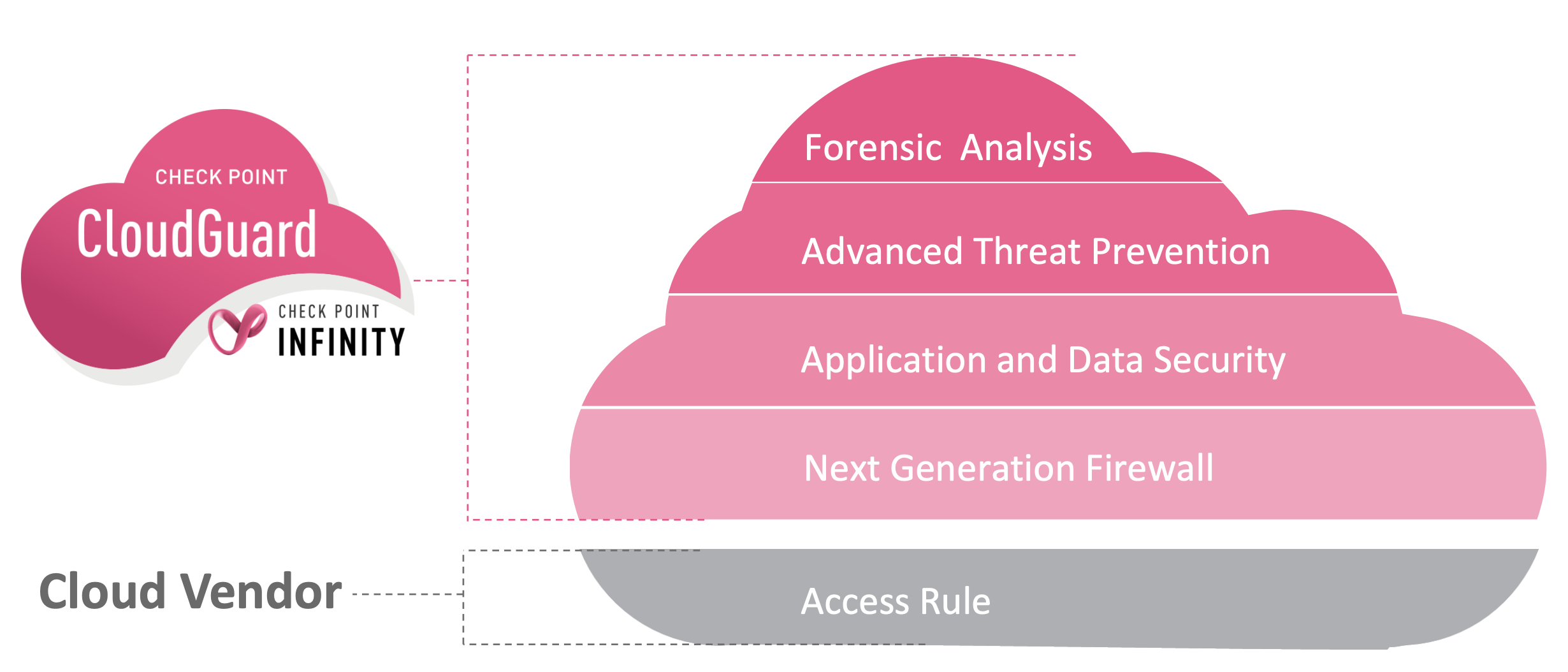
The cloud itself offers minimum security at level 4 using iptables, but we need much more. On the following figure, we can see the difference between the security provided by the cloud and that provided by the Check Point manager.
The next concept he explained was the perimeter, the fact that we do not have control over all the elements of the cloud. For example, storage may be separated, so that the firewall can no longer protect it. The security we have defined so far is not enough and the only way to obtain control is by defining configurations. Raul explained that these configurations are very complex and it is very easy to make mistakes. This is where the Check Point Dome9 SaaS solution comes in. Dome9 allows us to ensure that we are working securely in the cloud; that we are not exposing to the internet what we do not want to expose (Compliance & Governance).
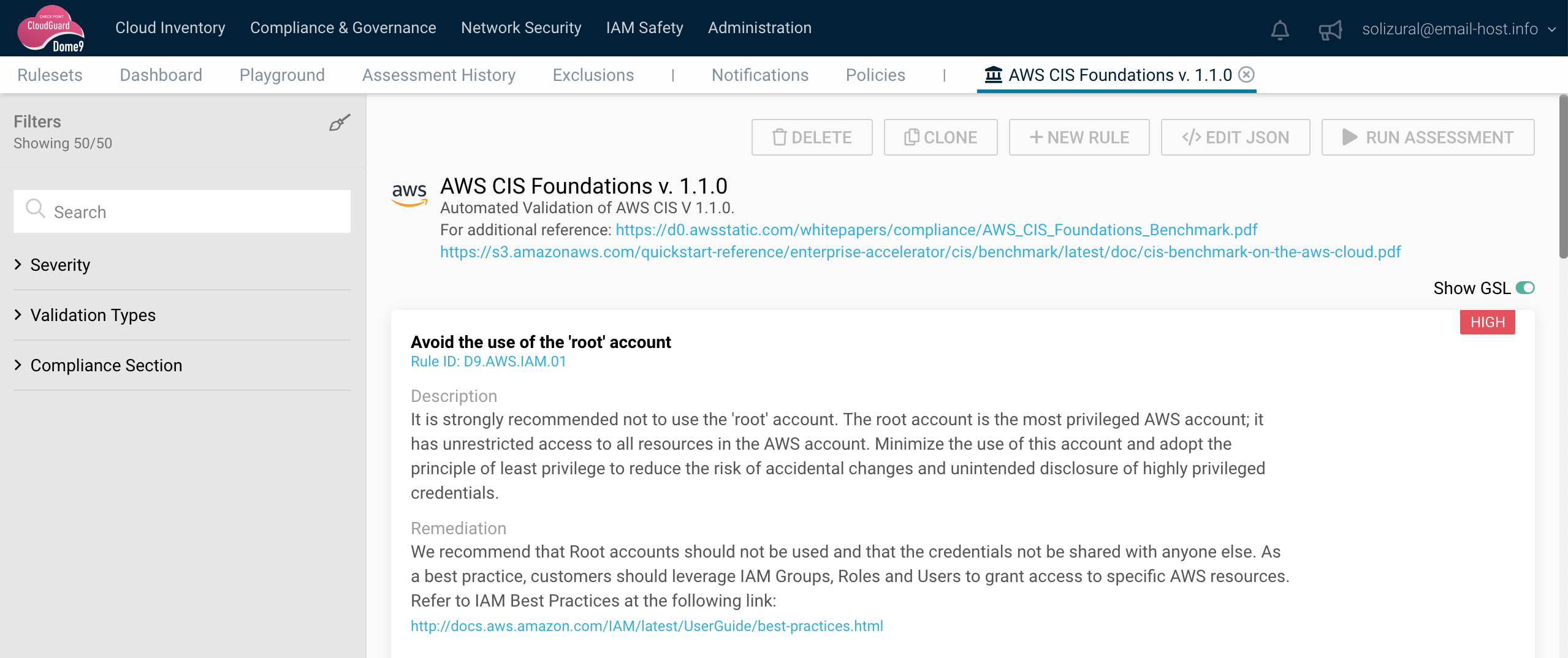
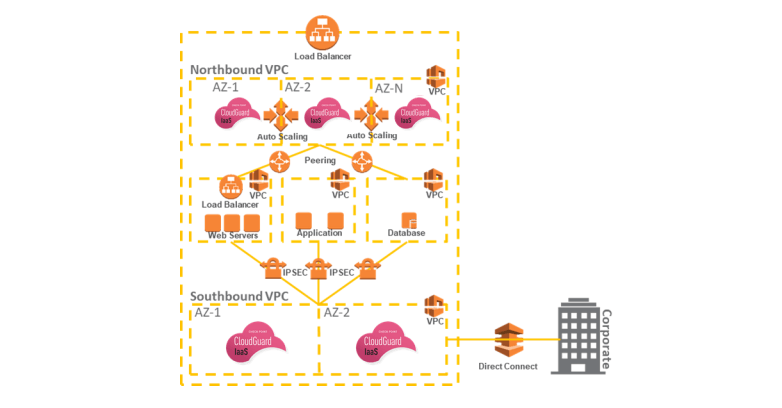
Dome9 generates reports that indicate the degree of compliance with regulations, risks, exposures, bad configurations, etc. This tool has two operating modes, read and read&write. With read mode it can only notify while with read & write mode it can alter the behavior, for example, delete an erroneous rule. On the following figure, we can see a diagram that shows the different zones that exist in the network as well as the objects that are in each one of them. In a visual way, it is very easy to identify if we have any security problems. Mention that we are talking about passive security since we are only reviewing configurations.

In conclusion, emphasize, in the same way that Raul did, the relevance of Dome9 in today's cloud environments. A firewall does not provide enough security in the cloud when there are elements beyond our reachable zone, that is, outside the perimeter.