What is SOAR?

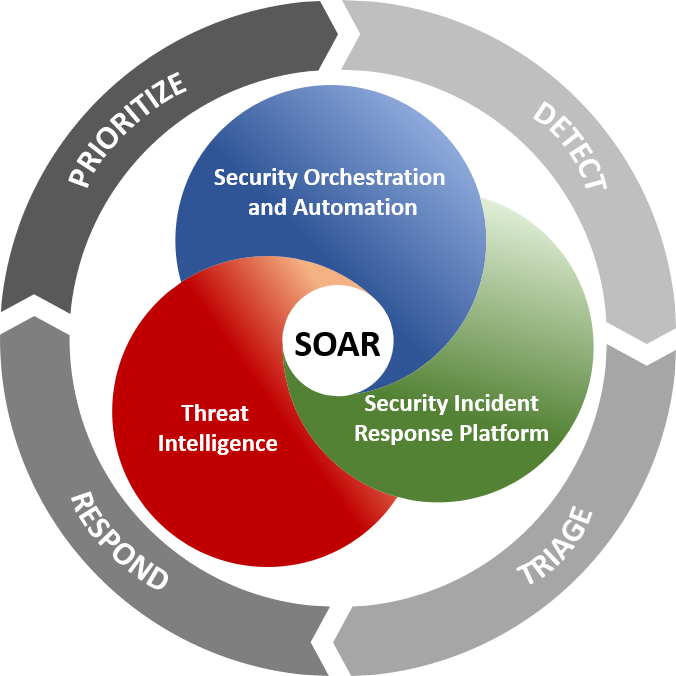
SOAR is a new acronym among the hundreds that appear every day in the cybersecurity market. It stands for Security Orchestration, Automation, and Response and is a category that began to gain momentum between 2015 and 2016, especially driven by Gartner.
When we talk about SOAR we must necessarily talk about other terms such as SIEM, UEBA, Threat Intelligence and this is because security teams have increased their visibility capabilities by incorporating these types of technologies or services within organisations, but the challenges (in terms of reaching maturity) that they are working towards are reflected in two fundamental aspects: being able to improve the workflow in relation to attending incidents and speeding up the response to these same incidents, which is why SOAR appears.
SOAR was designed to help security teams handle and respond more efficiently to threats through richer data coupled with automation of routine security tasks. To better understand what SOAR is all about, let's talk in more detail about its three components:
The first component is Security Orchestation which refers to the possibility of coordinating security tools and other types of technologies, which do not necessarily have to be security tools, that are normally used independently, even from different vendors, so that they integrate and communicate to establish an effective, efficient but above all iterable incident response workflow. Even with SOAR, data can be extracted from external sources to enrich the alerts we receive.
Security Automation is closely related to orchestration and is the method of automating manual tasks and processes, i.e. without human intervention. At this point it is very common to use the term playbooks, which are nothing more than linear tasks or steps containing basic actions based on conditionals.
As a third step we talk about Security Response. This point is the icing on the cake provided by SOAR, as security teams face one of the biggest problems in incident management to effectively close breaches. With the consolidation of orchestration and automation, taking specific actions such as quarantining a workstation, blocking an IP address, disabling a user account... the average response time is drastically reduced.
Having discussed each of the three components, it is important to highlight the key features that will help to better understand SOAR and, if necessary, select a SOAR platform:
1. Data collection. This refers to the collection of data or alarms from different platforms to enable equipment or even provide additional context related to the alarms.
2. Case management. The tool should allow the user to investigate and perform the relevant analysis at a single point. This dynamic makes the handling of incidents or threats across the organisation much more visible.
3.Playbooks. Automated incident response flows to speed up response times and definitely facilitate a more effective response within an adaptive security model. Some SOAR technologies come with hundreds of pre-defined flows for most common threats even based on models or frameworks such as mitre attack.
In summary, using SOAR within a security strategy allows you to:
- minimise risk as a result of a security incident
- reduce the time from the time a breach is discovered until it is resolved.
- Improve the effectiveness or efficiency of security operations or software.
Rafa & Alba