Routing i Switching protocols in Data Centers

To begin with, it must be said that the Routing or Switching protocols used in Data Centers can vary depending on many factors, one of the main ones is the topology that you want to implement when designing a Data Center, for example, the protocols to be used will change depending on whether you want to implement a two-layer topology such as "Spine and Leaf" or a three-layer one such as "Core-Distribution-Access". In addition, it can also vary if you want to make a design implementing "End of Row" or "Top of the Rack". In this post you can find more information about the designs
Apart from the topology, routing or switching protocols will vary depending on the equipment you want to use, since manufacturers usually recommend specific protocols which work much better with their equipment, or directly implement their own protocols adapted to the devices that make. For example, if you decide to use HP equipment, it is recommended that you use BGP and VXLAN as routing protocol, and MLAG, TRILL or IRF as switching protocols. But HP not only recommends these protocols because they adapt very well to their equipment, but also recommends using a topology of "Spine and Leaf" combined with "Top of the Rack" which complements these protocols very well.
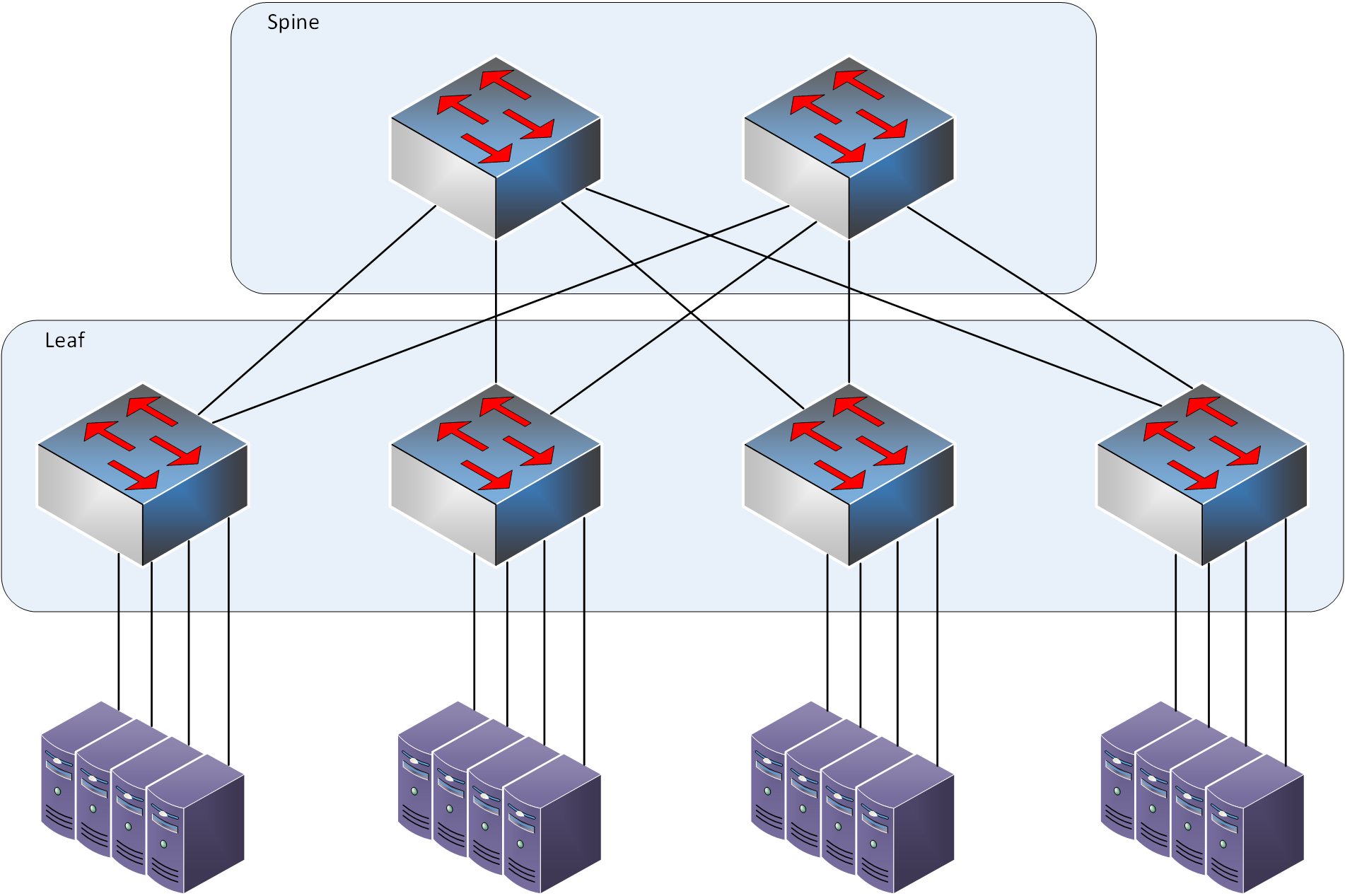
Implementation of a Data Center with "Spine and Leaf" connecting each Leaf with its servers.
In order to choose the protocols that best suit a Data Center design, many factors must be considered, such as the type of Data Center, the scalability, the costs of the equipment, the topologies, and the designs of the racks. Since there are protocols that work best in three-layer topologies or protocols that work better in two-layer topologies. On the other hand, scalability must be considered, since protocols should be chosen that, when extending the equipment, continue to function correctly and do not present problems or limitations. You also must think if you want to maximize the layer 2 area or the layer 3 area. Since, depending on the design, the equipment used or whether future extensions are planned, it is better to extend layer 2 or expand layer 3.
Until now it has been spoken of that, depending on the design, the topology, the equipment or even the scalability, some protocols or others are used, but what are these protocols? Next, the most common protocols of both layer 2 and layer 3 will be shown.
Layer 2
- Port Channel: It is used to group physical links to form a logical one and thus be able to offer link redundancy.
- TRILL: Maximize the use of links by combining characteristics of layer 2 and layer 3.
- Ethernet over MPLS: Carries Ethernet packets over MPLS.
Layer 3
- BGP: It is a routing protocol that exchanges routing information between autonomous systems.
- OSPF: It is a "Link State" routing protocol that uses the "Dijkstra" algorithm to calculate the shortest path.
Since the current trend is towards virtualization in Data Centers, what better to implement it with SDN (Software Defined Networks), which allows greater control of the flow of data in the network. When controlling the network with software, the protocols now are controlled by a software that constantly controls the balancing and flow of the data to be able to modify it depending on the needs and thus achieve a better efficiency and performance.
To finish, say that there is no single solution when choosing the protocols that you want to use in the operation of a Data Center, there are no better protocols and worse protocols, but, depending on the function of this, or the devices and equipment used, depending on the topology and the proposed design, you can make combinations of the different protocols that exist to get the most out of the facilities.